Here are the Cybersecurity and Ethical Hacking Terminology glossary you have all been waiting for!
In this modern era of life, we are getting really attached and are mostly dependent upon the computer and its related electronic devices. Our lifestyle, work, and homes are totally digitalized with all of these devices. In fact, all of these devices have become a part of our life. Just suppose that you are working on your Personal Computer (PC) and suddenly your computer screen turns black but your system is running what would you do?
Actually, you cannot do anything rather than restart your PC but who knows that all of your personal data is being stolen and copied at the back end of your Operating System (OS). The person who might be stealing your data is called a hacker and the process that he is performing is called the Hacking process.
Contents
What is Hacking Terminology/Language?
The person or the hacker who attacks your system and steals all of your personal data uses some sorts of techniques which can also be named as the “Hacking Terms”. These terms are mastered by the hackers and then they use them to get into other people PC’s and perform all of the illegal stuff.
Unfortunately, we daily experience countless incidents of Information Hacking, Failing Businesses, Data Breaches, and Financial Theft. All of these concepts or procedures require a good knowledge of some of the Hacking terminologies or Hacking terms. As we are just a simple computer users we don’t know much about hacking stuff and get easily attacked by different hackers. Some of us believe and rely upon Antivirus Software and think that they are completely safe from Hacking.
Wherever as time is passing by and the world is gradually progressing in the field of technology. Just like that hackers are also updating their technology and creating new techniques to get inside your computers and hack them for their illegal uses. Therefore in order to keep yourself safe from hacking, you should know about some of the well-known hacking methods and terms which can harm your computer system.
The Well-Known Hacking and Cybersecurity Terms of 2022 (New Hacker Slang and Vocabulary)
Now I am going to provide you with some of the basic and well-known terminologies of Hacking which you can read and search to keep your devices safe from getting hacked.
These terms are listed below:
- Malware
- Spoofing
- Adware
- Brute Force Attack
- Bot
- Firewall
- White Hat
- Black Hat
- RAT
- Worm
- Phishing
- Distribute Denial of Service Attack (DDOS)
- Ransomware
- Encryption
- Zero Day Threat
- HTTPS/TLS/ SSL
- Botnets
- Payload
- Rootkit
- SPAM
- Cloaking
- Back Door.
Let’s discuss the terminology above in much more detail!
Malware
Malware is basically software that is specifically designed by hackers who were created for stealing any type of information from devices and hijacking computer systems. This Malware software is easily moved into the targeted Computer systems with help of Spams, hard drive, and USB Devices. This software goes by names which are Spyware, Viruses, Adware and Keylogger, etc.
Our guides to staying safe from Malware viruses:
- How to have a Malware-Free Windows PC.
- How to Remove Malware from your Windows PC (Malware Removal Guide).
- How to Know if your PC is Infected with a Malware or Virus?
Spoofing
Spoofing of IP and E-mail are very few and common techniques of hacking by different users globally. The E-mail spoofing affects the dunk or header of the e-mail which makes it appear legit. For Example, the e-mails which just appeared from the bank or any other source that the user trusts can be made and sent by any type of black hat hacker. The IP spoofing is an illegal packet that is sent with a modified IP which appears to be a host that can be trusted.
Adware
Adware is usually software that is used to track the browsing activities of a user which acts like spyware. It basically produces or generates the ads (advertisements) which are usually based upon the User’s most searched item or Browsing History. Some of this adware is malicious which is specifically designed for doing the pop-up ads which slow down your PC. The reason behind the slowing down of your PC is the copying of Personal Data, providing inputs, allowing phishing attacks and browsing history.
Brute Force Attack
This is another common hacking term that is used to bypass the login pages and get inside them. Brute Force is a method and error trial that is used to decrypt any type of data such as DES (Data Encryption Standards), passwords or any information which is encrypted.
Bot
This is robot software that works over the internet and runs the scripts (automated tasks). These bots are employed by the many popular search engines such as Bing, Yahoo, and Google. These bots are also called spiders. The purpose of these bots is to scan the websites and index them. The purpose of the index is to do the ranking according to the search queries. But these bots can also be used for performing malicious attacks and attacking a computer.
Firewall
A firewall is the security system for a network that Blocks out all of the non-trusted sources or items for safer communications and frequently oversees the outgoing and incoming traffic of the network. A firewall can be software-based or even hardware-based.
White Hat Hacker
The white hat is the technique that is totally opposite to the Black hat. As we know that Black hat is used by hackers for performing destructive actions. Whereas the White hat is used by the ethical hackers to reveal loopholes before they are exploited by black hats.
Black Hat Hacker
Black Hat Hacker is the persons or people who accomplish hacking for financial gains and other illegal purposes. These persons bereave into the network and perform Modification, ransom, stealing or destroying of data. This concept is based on the villain character because mostly they wear black hat.
RAT (Remote Access Tool/Trojan)
Remote Access Trojan or Remote Access Tool (RAT) is a Malware that can also be operated or used by the hacker even though if he is unskilled. The attacker gains complete control of the system if the RAT is installed on your computer. RAT is used for authentic purposes just like a computer user desires to access his home computer even from any other Location. But hackers mostly use it for unauthentic purposes.
Read also: AndroRAT APK Free Download – Android RAT App.
Worm
Just like a virus, there is another autonomous program that can be destructive and can self-replicate. A worm is not a part of a program, but it can transfer with the help of the network to multiple systems.
Read also: Top 4 Ways to Keep your Windows PC Safe.
Phishing
This is a very common hacking terminology that is mostly used by security professionals. Phishing tricks are used to reveal any type of sensitive information from the user this information can be (Credit Card detail, Usernames and Passwords).
This involves tricking the victim to handing in their login information by creating a fake web page. This page looks very similar to the original one. This can be a fake page to Hack Facebook Accounts using Phishing.
Distribute Denial of Service Attack (DDoS)
This is a cyber attack that has the intention to take a service down. This can include a website, app, or server. Denial of Service attacks is mostly caused by generating lots of fake traffic or requests to a web server that it cannot handle and shuts it down.
This closes the service and makes the end-users unable to access it. You can learn how to do a DDoS attack.
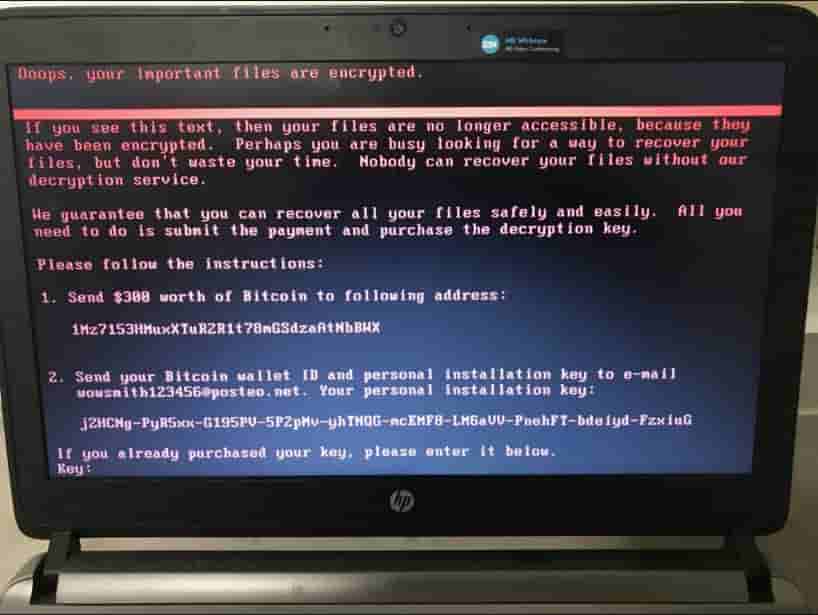
Ransomware
Ransomware was the most searched term for hacking in the year 2017. It is also malware that locks out a user from his own computer system or any other device. A message pops up over the screen which is basically a ransom message. It instructs you about how much and where to send the payment which is most requested in the form of bitcoins in exchange for your files. Learn how to stay safe from Ransomware viruses.
Encryption
This is a process which is used for encoding the information or message. The purpose of encoding a message is to ensure that the information in the message is only readable by the authorized person or the receiver.
Our top guides and articles to learn how to implement encryption:
- How to Send Encryption Emails in Gmail, Yahoo and Outlook.
- How to use AxCrypt for File Encryption and Data Security.
- How to Secure your Gmail Account.
- How to Password Protect Word Documents and PDF Files.
- Google Dorks List for Google Hacking.
Zero-Day Threats (0-day)
This threat is hidden from the antivirus software installed on the system and undocumented. This kind of defect is built in almost all of the anti-virus software which makes it ignorant for the Developers who had knowledge of these vulnerabilities and build these antivirus functionalities.
HTTPS/TLS/SSL
This is also a very popular searched terminology in 2018. It became popular when Google Chrome Browser declared that they will warn the users who open the HTTP using websites. HTTPS stands for (Hypertext Transfer Protocol Security) it controls the whole process of how the data is transferred across the Web. TLS and SSL are also the protocols that are used by HTTPS. It helps to protect websites from being hacked and adds a layer of encryption.

Botnets
This is a whole network of bots that are being controlled by the black hat. There are several applications which the Botnets include within them. These applications are DDoS, allowing hackers to access devices, steal data and send spam. The endpoints that are hacked by the Bot network are called Zombies.
Payload
It is baggage of all the sent data over any type of network. The black hat is a hacking terminology which is referred to the virus or the part of it which performs the malicious attack such as copying data etc.
Rootkit
These are the very alarming methods which are used for performing cyber interruption or cyber intrusion because it is not detectable. A black hat can perform a perfect heist if he had access to the rootkit. It is a malware program that can easily be installed on your computer right in front of you and you wouldn’t even be able to detect it.
SPAM
This terminology is related to E-mails and different messaging sites. SPAM itself is an E-mail that is used for spreading advertisements with the help of E-mails. Some of these E-mails might even contain some malware within them which will activate if they are opened.
Cloaking
This term is mostly used by hackers for presenting the different types of URLs or contents to the search engines and the user. Hackers use .htaccess and dynamic scripts which helps them in hiding their tracks because it returns 500 or 404 error code to many browsers.
Recommended Read: How to Keep Your Kids Safe Online (Online Safety Tips for Kids).
Back Door
It is a hidden passage that leads into a computer by bypassing the traditional protection of the Passwords and logins, which makes it a whole lot easier to gain access to a targeted computer. Back doors can give full access to the end-users system.
Script Kiddie
This is someone who doesn’t have much knowledge about hacking at all. These are people that use other people’s scripts or modify them slightly for their own purposes instead of making their own hence the name “Script Kiddie”. They are usually hackers who deface websites and attack small networks.
Update: These are now also available in PDF.
Wrapping Up
In this guide, we discussed the best hacking terms which are popular among hackers and security specialists. We further discussed these terms and talked about their working and their functionalities. But before I end this article I would like to give you a piece of advice. I shared this information so you can use it for your own security purposes instead of using them for hacking. Use this as a resource and bookmark it!






