
As we are living in a digital era today, credentials play an essential role. We use it to protect our data, photos, information, and much more. It’s the lock to our life online.
At times what we do to save out time is choose a simple one that can be cracked easily by anyone out there. You can become a victim of a cyber-attack, and personal information can get leaked. This page details the top 100 most common passwords 2022 list that includes the worst passwords ever chosen by people!
To protect yourself from such a hassle, you need to use one that is unbreakable, random, not guessable, and unique. Keep reading below to find out what makes a good and strong password. We also share tips on avoiding silly mistakes when choosing one!
Contents
Most Common Password mistakes made by people
People tend to use the same password to log into various accounts they have. Like you use fb1902 to access an account and use the same to sign in to Hotmail. If your Facebook credentials are exposed, then hackers can access the details of related accounts.
Moreover, at times, we put all our details in a folder and name it passwords; this can be accessed quickly and get known by the hacker.

- 123456: This one is most commonly used. According to a survey, it has been found 23 million times in various data breaches.
- 123456789: Another commonly used is “123456789”, which was used by 7.7 million users.
- “qwerty”: Third most commonly used password is “qwerty”. Around 3.8 million users have been using it.
- “Password”: Around 3.6 million people are using this—what a shame.
- “1111111”: Around 3.1 million people using this. My expectations are already low after reading this statistic.
SEE ALSO: What is THC Hydra and How you can use it.
How much time is required to crack a “Good” and “Bad” Password
The below infographic will give you details on the timescales of such attacks:
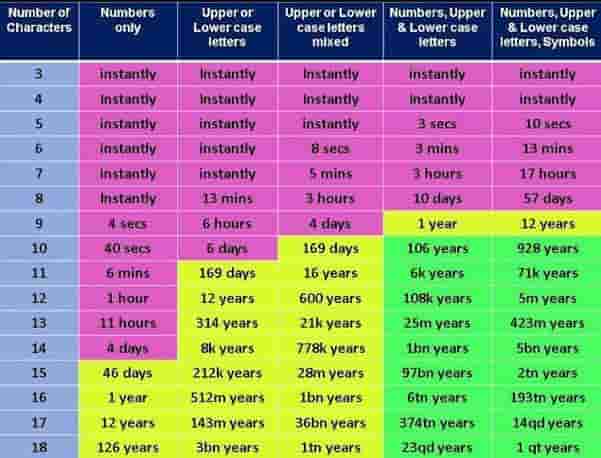
Top 100 Most Common Passwords (2022 Ultimate List)
These are as followed; if yours is there on the list, then you need to change it immediately to save your private data. The below infographic list shows you the 100 most popular passwords in use today:
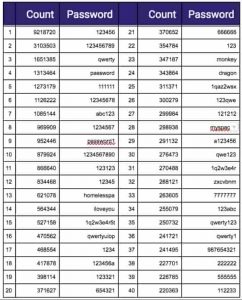
Recommendation: The reason why you should AVOID such easy passwords is that they can end up in text files that have them included as a result of a breach. One popular example is RockYou.txt.gz. People with malicious intent can then use it to brute-force your social media account passwords or any other online service they may suspect you to be using.
Top 50 most commonly used passwords
These are as followed:
- football
- iloveyou
- admin
- welcome
- monkey
- login
- starwars
- 123123
- dragon
- passw0rd
- master
- hello
- freedom
- whatever
- qazwsx
- trustno1
- Password
- 123456
- 123456789
- Qwerty
- password
- 1111111
- 12345678
- abc123
- 1234567
- 1234567890
- 9876543210
- password1
- 12345
- letmein
Screen Lock Combinations that everyone knows
Lock combinations can also be cracked very easily. Some are listed below, if you are using any of these then make sure to change them to be safe and secured. Alternatively, we also have a tutorial that shows you how such a combination is bypassed.
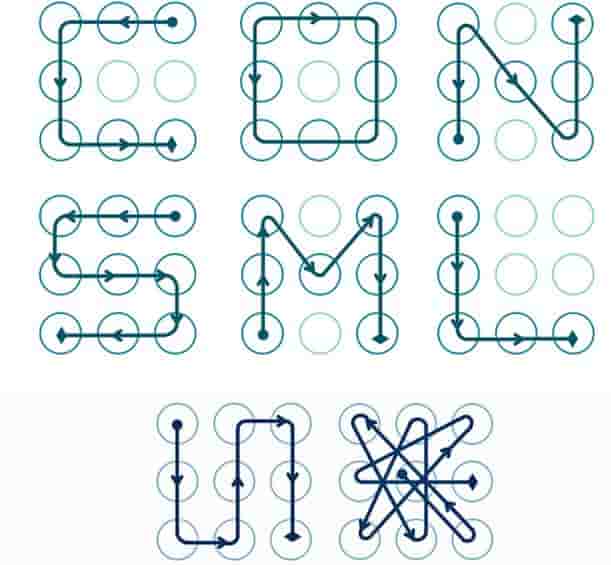
SEE ALSO: What is File Encryption and why AxCrypt should be your #1 choice.
Common Passwords found on iPhone
Read the below graph that showcases the top 30 most commonly found pin codes on an iPhone device:

SEE ALSO: 10 Free Password Cracking Tools for Windows and Linux.
Protect your passwords as you protect your life

- Avoid using the same to log into various accounts.
- Use a password manager that is used to encrypt and store them in a secured vault which is protected by a master password and you shall remain safe.
- Do not use the ones that have been mentioned above.
- Use one which is a combination of alphanumeric, carries special characters, symbols, lower case, and upper case alphabets.
As mentioned above the length matters a lot, have upper case and lower case letters, numbers, symbols, no ties to any personal information, and no dictionary words as well. You do not need to memorize all these letters and numbers to incorporate all such aspects you need a few tricks, and you are good to go.
SEE ALSO: Default WiFi Router Password and Usernames List.
How to see if a password is weak
Let’s tell you a secret; you need to make passwords memorable but hard to guess. Learning some tricks would help you. Creating them can be a lot of fun and pay off in increased safety is enormous.
Let us see some common examples to understand why these put you out at risk.
- Use of common words such as “Password” or “1234567890”
This is the most comply used one which is pathetically weak- as are default and blank. If we look at them, these are simple words that can be guessed within seconds. Keep in mind that humans are not the only ones that would concern you. Still, programs that use automated databases can perform a dictionary default on the system and thus identify it quickly.
- Be aware of Social Engineering and never pick something common
A typical example is you use the last name with your year of birth combinations such as John1234. Now, although this is a combo of 8 words which includes letters and numbers as well, it carries a name that is associated with you or your family and some other identifying pieces of information like your year of birth. All this is very easy to hack.
- Keep it long and confusing
If you use H4CK3R, mix up with numbers and capital letters. Following are the reasons why this is not safe:
- Several substitutions can be guessed easily. Adding the number 1 for the letter, it is easy to guess for any software or humans out there.
- It is relatively short as you can see, long ones are considered to be healthy. The harder a hacker has to work to break, the better.
SEE ALSO: Download Wfuzz Free – Web Application Cracking Tool.
4 Essential Online Password Tips you need to know
If you have settles on one that has a perfect length, obscure, and carries letters, numbers, and cases then you are on the right road, but it does not mean you are fully protected. Keep the following things in your mind:
- We recommend that you do not reuse it; If you are using the same one everywhere across shopping to sites having personal details, then you need to things over it as if anyone is accessed the others are the risk too.
- Try avoiding writing them anywhere, e.g. Desk or Chair; If you plan to do something like this then keep in mind that consequences can be discovered easily.
- Use Password Manager; many apps are used to protect them. Webroot SecureAnywhere Internet Security Plus and Webroot SecureAnywhere Complete provide one as an additional online tool for security. My recommendations are 1Password or LastPass.
- Sharing is not caring when it comes to credentials; Never trust anyone, period! This is one rule you need to imprint on your brain.
- Have secret meanings that only you can guess: Following examples let users use phrases that mean something to them or are associated with the type of site. Like “the all for one and one for all” may be for social networking sites whereas “it’s all about sharing” may be a phrase regarding money for a banking website and much more. Some more examples are:
- 2B3orN54ewot2B_ThdsfdsatIsThe? – (To be or not to be, that is the question – from Shakespeare)
- L65r_L832rNsdfsdfot2day – (Later, later, not today – from the kid’s rhyme)
- 456Score&743rweryrsAgo – (Four score and seven years ago – from the Gettysburg Address)
- John3:dsfsd16=4G – (Scriptural reference)
- 1894A&7A41d45gumaS – (one for all and all for 1 – from The Three Musketeers, by Dumas)
Following examples tell a story of using the same style so if you know to write the first sections, and you are there on the login page for a website then shall know what to add
- ABTlki2_uz_AMZ! – (About to use Amazon)
- ABT2dfs_uz_BoA! – (About to use Bank of America)
- Pwrd4mnbfcct-$$ – (Password for an account at the bank)
- Pwrd4Adfscct-Fb – (Password for a Facebook account)
Most of the system keyboards carry around 101 to 105 keys; users have many options when it comes to creating a password that is unique and difficult to crack. Keep in mind that you do not need to think of it as numbers rather think of it as a canvas on which you have to perform your creativity.
SEE ALSO: How to Download and Use Wep0ff for Finding WEP Pin.
Add Emoticons – Why not?

Some websites limit the types of symbols they can use while others allow a wide range. Try to make your characters memorable by turning them into smiley faces to boost power instantly. 9qazdrfvtgujmgy7, now if we look at this one, this is quite hard to remember unless you know that it makes a W on your keyboard. This way, it becomes easy to remember. You can make letters, shapes and much more just by drawing on it.
Use commonly allowed symbols
Users can use basic smiley faces to create long, strong, and memorable mixed-character passwords using these tricks.
![]()
Password Cracking Tools that are the main culprit behind
These are tools that use your CPU or either GPU with the help of complex algorithms that try a pattern of words, letters, numbers, and characters to guess from a huge password list file. Here are some well-known examples in the wild:
- John the Ripper – the oldest cracker in the game.
- Medusa Password Cracker.
- RainBowCrack – Rainbow Tables Cracking Tool.
- Hashcat – Most popular MD5 hash cracking utility.
- What is Brutus Password Cracker and How to Download it.
3 Most significant Data Breaches that happened because of weak passwords
Below are the three most impactful breaches that happened to various companies because of using one of the worst ones ever!
- Adobe Friend Finder
This one was sensitive for account holders. FriendFinder Network which carries sites like Adult Friend Finder, Penthouse.com, Cam.com, and Stripshow.com got breached in October 2016. Stolen data spanned around 20 years on six databases and took names, passwords, and email addresses.
Source: Information Age.
- MySpace
In 2016 it made the news after 360 million user accounts got leaked on both LeakedSource and put up for sale on the dark web market. Lost data had email addresses, passwords, and usernames for some performances, according to WeLiveSecurity.
- NetEase
It is a provider of mailbox services via likes of 163.com and 126.com. It carried email addresses and passwords of almost 235 million accounts of customers which were sold by a dark web marketplace vendor called DoubleFlag.
Alternatively, you can also have a look at the Pwned Websites, which is a frequently updated list of sites that have suffered a breach.
Which Common Password have you ever used? – Be Honest
Just admit it. We have all used at least one from the above list of most common passwords! Some of these are the worst passwords I had ever seen that can be guessed in a matter of minutes using a wordlist.






