If you want to get information about DroidSQLi Android App and how to use it for good purposes then you came to the right place. As we see nowadays hacking is impossible to be done. Especially, hacking websites is getting impossible day by day. So today we are going to talk about how to hack a website’s database and take out the required information out of that website by using an Android app named “Droidsqli”. Before we start the complete detailed information about DroidSQLi, let’s talk about SQL injection.
Contents
What is SQL Injection?
So, basically SQL injection is a technique that is used to inject the code into data-driven applications, these applications are attacked by injecting (inserting) the SQL statements into an entry for execution (e.g to depot the database of the attached application to the attacker).
In simple words, if you master this technique you can approach a website database. You can access the Passwords, Usernames, Changing Webpages, Credit Card transactions, in other words, you become the controller of the whole Website. It is a huge defect and can damage the whole Website.
You can attack vulnerable websites with the help of SQL injection. You can find such a vulnerable site by using Google dorks. You have to type the following on the search bar: “inurl news.php?id=”. After you type this and press enter it will search and display you the vulnerable links.
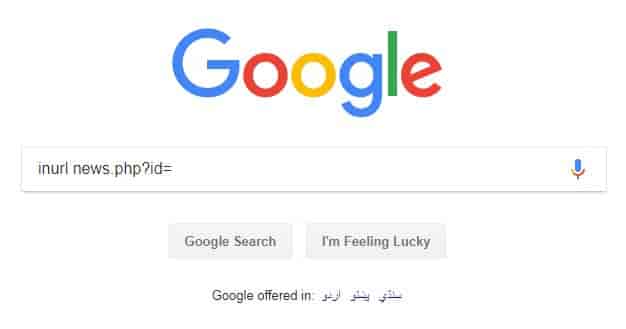
Example: http://www.mysite.com/news.php?id=
When you click this link it will open the vulnerable website. When the site has opened the first thing you have to check is that is this Website vulnerable for the SQL injection. To check this you have to open the URL on the top of the site and type an ‘a’ at the very end of URL. As you press Enter a warning message will be displayed which will be like:
- Warning: mysql_num_rows()
- Warning: mysql_fetch_assoc()
- Warning: mysql_result()
- Warning: mysql_fetch_array()
- Warning: mysql_numrows()
- Warning: mysql_preg_match()
If you see these warnings this means that the site you targeted is vulnerable. This means that the site you searched can be infected with the SQL Injection.
As we have found a vulnerable site so now we can attack it by using the SQL Injection app for Android called “Droidsqli”. In order to use Droidsqli, you must have an Android device (e.g Android smartphone).
Also read: AirJack Packet Injection Software Free Download.
So, now we will discuss Droidsqli.
What is Droidsqli? – (Explained)
As we know about SQL Injection so it will be easy for us to understand Droidsqli. Basically, Droidsqli is an application made for the Android platform which can be used to perform SQL Injection in a vulnerable website that you want to attack.
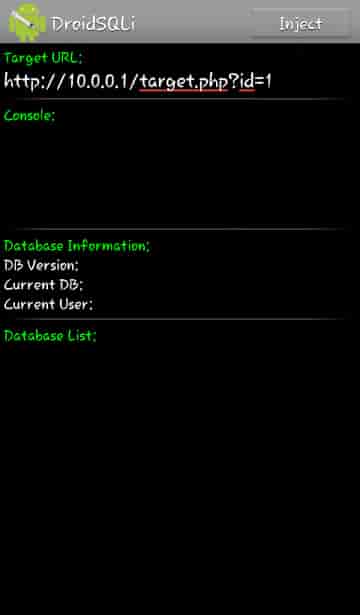
So, first of all, you have to download the Droidsqli for your Android device and in order to install it correctly make sure your download from unknown sources is checked in your settings. When you have finished installing Droidsqli go to your applications menu and open it. Once the app is opened type or paste the URL of the Website you want to attack in the target section of the app.
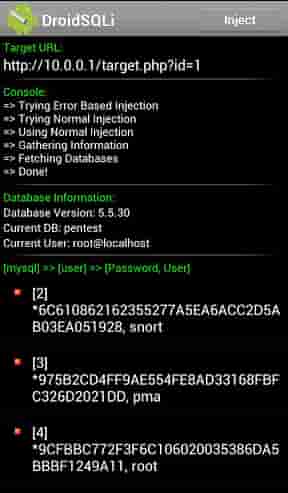
After pasting the URL press the Inject button at the top of the app and wait for the app to complete the process for you. If it completes the process, then it should display you the name of the databases. You can select any database and take out the desired data you need.
Look at the screenshot below, you will have a similar one displayed on your device.
Seeing the different ways it can attack a victim.
Also read: Acunetix Web Vulnerability Scanner Free Download.
SQL Injection Techniques supported by Droidsqli
Now we are going to discuss the Injection Techniques supported by the Doidsqli. By using these techniques we can attack the Website we want to attack. These techniques are named below:
- Time-based SQL injection.
- Blind SQL Injection.
- Error Based SQL Injection.
- Normal SQL Injection.
All these techniques work within a unique manner and perform the same task that is to hack a targeted website and take out all of its information.
Now I am going to explain all of these Injection techniques which are listed above.
- Time-Based SQL Injection:
Time-Based SQL Injection is generally used to attain tests while you cannot find any other way to fetch data from the database server. This type of attack inserts (injects) a SQL Statement that contains a definite DBMS function or query that can cause a time delay. It completely relies upon the time in which it gets the server response, it may possibly subtract some information. This type of interference path is especially useful for Blind SQL Injection attacks. A very basic test “Determining if the vulnerability is present” can be achieved by the use of Time-based attacks. This is a very good option when the attacker is covering a blind SQL injection. In such a position, only interruption functions or procedures are essential.
- Blind SQL Injection:
Blind SQL Injection is a technique in which the data based is asked for true or false questions and demands for the answers according to the application’s response. This technique is usually used when website or web application is constructed to display generic error messages, it doesn’t lighten the code which is vulnerable to SQL Injection. When the SQL Injection is exploited by the attacker, the error messages are displayed by the website or application. These error messages are of a database that complains that SQL Query’s Syntax is faulty.
- Error Based SQL Injection:
Error Based SQL Injections are oppressed due to the errors triggering the database when false inputs are entered into it. This technique is useful when the vulnerability of SQL Injection cannot be exploited by the tester. This technique forces the database to perform a few operations due to which it will be an error. Then it will try to draw out some data from the database and display it in the error message.
- Normal SQL Injection:
We have talked deeply on this technique and it is explained above. As a recap, I am going to explain a few important points about Normal SQL Injection. Normal SQL Injection is the attack that is done by injecting the malicious SQL Query in a website or an application and then it will give you all the database of that website or application.
Also read: Metasploit Pro Framework Free Download.
How to Use DroidSQLi (A beginners guide)
You have asked various times on how you can use it! It’s pretty simple and straightforward, follow these steps:
- As you can see from the app screen it asks for a “Target URL”.
- Pick a target – Please make sure it is a test environment and you have permission.
- Reconnaissance: This is where the tab with “Database information” comes in handy as it will tell you if it’s running MySQL, MariaDB or MongoDB.
- The last tab is where the actual “hacking” as we call it takes place. It now runs a number of Google SQL injection dorks. These are a number of strings and queries that find vulnerabilities in the DB which will further show you the username and password.
DroidSQLi Latest Android APK Free Download 2021/2022
So that was all the information you needed to know about SQL Injection or Droidsqli. Droidsqli is very easy to download and install you just have to follow the instructions that I gave you in the above explanation. I am also going to add a link so it will be easy for you to download and install Droidsqli Apk on your Android device for free!.







Dude, this is the only one that actually works, thank you!