Secure Shell or secure socket shell was also known as SSH is a network protocol. It gives the user, particularly system administrators, the way that is secured to access a computer over an unsecured network. It refers to the suite of utilities that implement the SSH protocol. Today we will show you how to enable Windows 10/11 SSH command line.
It provides strong authentication and encrypted data communication between the two computers over an open network, just like the internet. SSH Windows 10/11 Command Line is a new feature that came included in an update. It is used mostly by the network administrators to manage systems and applications remotely, thus allowing them to log into another computer over a network. It is used to perform commands and move files from one computer to the other.
Contents
What is SSH (Secure Shell)?
The secure shell refers to:
- Cryptographic protocol
- A suite of utilities that implement the protocol.
The secure shell uses the client-server model, and it connects a secure shell client application at the end of which the session is displayed along with an SSH server at the end of which the course runs.
Implementations of the secure shell include supports for application protocols that are used for terminal emulation or file transfers. Secure tunnels are produced by SSH for other application protocols like for example: if you want to run securely X Windows system graphical sessions remotely, the secure shell server listens on the standard transmission control protocol (TCP) port 22 by default.
You can use SSH with ordinary user ID and password as credentials; the secure shell relies on public key pairs to authenticate hosts to each other. ID and Password must be used by individuals to connect to the host itself. If we talk about the local machine and the remote machine separately authenticate to each other. This is done when a unique public key is generated for each host in the communication. Two public key pairs are required for a single session. They are used for:
- The first key is used to authenticate the remote machine to the local machine
- The second key is used to authenticate the local machine to a remote computer
To secure communication between different types of the local machine and a remote host, the SSH connection is used. It also includes:
- Secure remote access to resources
- Remote execution of commands
- Delivery of software patched and updates
- Administrative tasks &
- Management tasks
SEE ALSO: Download DarkComet-RAT for Windows 10/8/7.
How to Turn on Windows 10/11 SSH in Command Line/Command Prompt
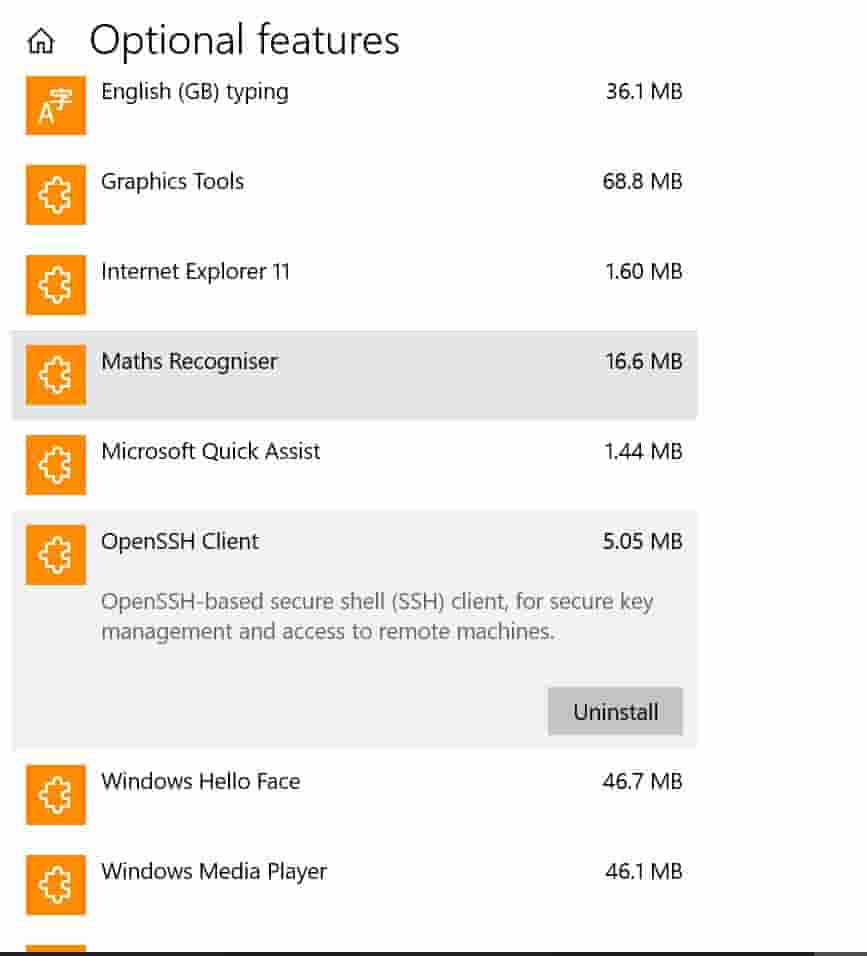
To enable/config SSH for Windows 10, follow the steps below:
- Open Start Menu.
- Now navigate to ‘Manage optional features.’
- After you navigated to optional features, select ‘add a feature.’
- Now scroll to the bottom of the features page, and you will see ‘OpenSSH Client.’ You can read more about OpenSSH on this website.
- Click on it and select Install.
Secure Shell Features on Windows 10/11
The secure shell enables the following functions:
- Has automated file transfers
- Has secured file transfers
- Issuance of commands is secure on remote devices or system
- Has secure management of network infrastructure components
- It has interactive and guaranteed file transfers
- For users and automated processes, it has secure remote access to SSH enable network systems or devices.
The secure shell is used to enable terminal sessions. It should be used instead of the less safe Telnet Program. The secure shell is used to allow for programs and systems to remotely and securely access data and other resources in scripts and other applications.
SEE ALSO: How to Fix Failed to Enumerate Objects in the Container Windows 10/11 Error.
How Secure Shell Works in Windows 10/11
To replace insecure terminal emulation or login programs such as Telnet, rlogin (remote login) and rsh (remote shell), Secure Shell was created. It is used to enable the same functions, which include logging and running terminal sessions on remotes systems. The secure shell is also used to replace file transfer programs like FTP (File Transfer Protocol) and rcp (Remote Copy).
The secure shell is used to connect a remote host for a terminal session. The command format is as follows:
Using the ID and password, this command will allow the client to connect to the server name server.example.com. If this is the first time a connection is being established between the local host and the server, the user shall be prompted with the remote host’s public key fingerprint and prompted to connect, if there has been no prior connection then the authenticity of the host that is ‘sample.ssh.com’ cannot be established.
DSA key fingerprint is 01:23:45:67:89:ab:dd:ef:fs:fe:dc:ba:98:86:54:12:10.
Then you have the following question:
Are you sure you want to continue connecting (yes/no)?
If you answer this with a “YES,” then it causes the session to continue and stores the host key in the local system’s known_hosts file. Moreover, the data is hidden and by default is stored in a hidden directly that is known as /.ssh.known_hosts, in the user’s home directory. As the host key gets stored in the known_hosts file, the client host cannot be directly connected to that server again without the need for any approvals. The host key is used to authenticate the connection.
SEE ALSO: How to Convert Excel Files to Vcard VCF Files (Free Online Converter).
Some Issues with SSH
The enterprises that use secure shells consider finding ways so that they can manage host keys that are stored on client systems. The keys can be accumulated over time, especially for the IT staff that needs to be able to access remote hosts for management purposes.
The reason is that the data stored in an SSH known_hosts is used to gain access to a remote system, the organizations, however, need to be smart in terms of this and must know the existence of these files and must have a standardized process for retaining control over these files.
The developers must also work with care when they are incorporating SSH commands or functions in a script or any other type of program as it is possible that an SSH command can be used which includes a user ID and Password to authenticate the user of the local machine to an account on the remote host when you this it opens the chance to expose the credentials to an attacker with access to the source code.
If we look more into it we get to know the shell shock which is a security hole in the bash command processor, can be executed over the SSH but is a vulnerability in bash, not is SSH. Poor key management is the biggest threat to SSH. The organizations can lose control over who has access to which resource and when if there is not any proper centralized creation, rotation, and removal of SSH keys.
SEE ALSO: 14 Best Free Typing Software for Windows 10 & 11 (Download).
SSH vs. Telnet – Hint: Secure Shell Wins
The first internet application protocol was Telnet; the other includes the FTP. To initiate and maintain a terminal emulation session on a remote host, Telnet is used.
Both secure shell and Telnet are similar when it comes to functions with a slight of difference that is the SSH uses public-key cryptography to authenticate the endpoints when setting up a terminal session as well for encrypting session commands and outputs.
On the other hand, Telnet is used for the Terminal emulation. SSH is used for terminal emulation as well to issue commands remotely as with rsh, transferring files using (SFTP) SSH file transfer Protocol and for tunneling other applications.
Why you should be using SSH on Windows
Now, you can use SSH for many purposes. These are as followed:
- This allows you to move across your hosting account file structure.
- You can monitor live the log files and start and stop service (dedicated and VPS customers only)
- By this, you can install software to your account
- You can manage your MySQL databases
It allows the user much more to do than just a standard web-based graphical interface allows. Some of the content management systems like Word press CLI and Drupal’s Drush have their command-line interfaces.
SEE ALSO: How to Fix USB Device Not Found/Recognized Error in Windows 10/11.
Benefits of using SSH in Windows
It has the following advantages:
- IP address spoofing – keeps the source computer’s identity and location a secret.
- Sniffing the transmitted data – the attacker can watch the data that goes around if you have an insecure connection, with SSH they can’t!
- Data manipulation at routers along with the network- the attacker changes the data along the network route.
- DNS spoofing – here the data is inserted into a domain name system which causes the name server to return an incorrect IP address, so the traffic is diverted to another computer.
- IP source routing– used by malicious users to fool the machine that it is talking to a different one.
- Encryption – This is one of the biggest advantages as it encrypts your data. This means that no MitM attacks can occur.
Quick tip:
If you see errors like ‘Windows 10 ssh not recognized‘ and ‘cannot install OpenSSH‘. Try to reboot your PC and try again or install the latest Windows updates to fix the issue. I would suggest being on the latest Windows 10 1903 update.
Big update:
Windows 10 is now supporting SSH natively and it is still in early beta. To enable it, follow the below steps:
- Open the Windows start menu and type “Manage optional features“.
- Now click on “add a feature” and search for “OpenSSH Client” and add it.
SEE ALSO: How to Remove Windows 10 Activation Watermark Permanently.
Do you SSH into Windows 10/11?
In this guide, we have discussed with you how you can enable SSH on Windows 10/11. We have discussed the benefits it provides as well as the security issues the user might undergo. SSH in Windows 10/11 command prompt helps you quickly get access to your personal machine from anywhere in the world using just a terminal and an internet connection. I recommend you to read our Linux server hardening guide before enabling SSH.
If you found this tutorial interesting do let us know by commenting in the section below.